ICO Artificial Intelligence Audit
ICO Artificial Intelligence Audit
As you will remember, we explained what is artificial intelligence audit and some different frameworks suggested for auditing AI in our article which is “Artificial Intelligence Audit”. In this article, we will focus on a guide developed for artificial intelligence audit, which is named as "A Guide to ICO Audit: Artificial Intelligence (AI) Audits".
As the name suggests, this guide was published by the Information Commissioner Office (ICO) in May 2022. The ICO “is the UK's independent body set up to uphold information rights.” [1]. Audits will be implemented by ICO’s Assurance department.
Consensual and Compulsory Audits
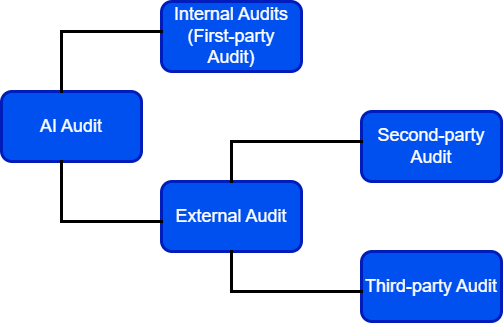
The guide suggests two kinds of audits, which are identified based on whether the audit is mandatory or not: consensual and compulsory audits. As you will remember from our article “Artificial Intelligence Audit”, dividing audits into kinds based on the auditor's relationship with the auditee is also possible: first-party, second-party and third-party audits. According to this classification, the type of audit discussed in the guide is a third-party audit since it will be conducted by a third party which is the ICO.
The ICO has the authority to conduct both consensual and compulsory audits, which is provided by Data Protection Act 2018 (DPA 2018). The provisions in S129 of the DPA 2018 enable the ICO to conduct a consensual audit which is the kind that ICO mostly conduct [2]. On the other hand, a provision in S146 of the DPA 2018 enables the ICO to conduct compulsory audits [2]. S146 authorizes ICO to issue assessment notices and requires controllers to permit the ICO to evaluate whether they are compliant with data protection legislation [2].
.png)
Key Notes
- According to the following factors, ICO will identify the high-risk controllers and develop a programme of audits:
- “reported breaches;
- the number and nature of complaints received by the Information Commissioner;
- controllers’ annual statements on control and other publicly available information;
- business intelligence such as media reports and;
- other relevant information.” [2].
- According to the following factors, the potential effect of non-compliance will be evaluated:
- “the number of individual’s potentially affected;
- the nature and sensitivity of the data being processed and
- the nature and extent of any likely damage or distress caused by non-compliance.” [2].
- The guide classifies the organizations that might be audited into five categories:
- voluntary organizations;
- organizations determined by the risk assessment process;
- organizations providing relevant learning opportunities in terms of ICO’s areas of interest; which are determined by research;
- organizations determined as “potentially benefiting from an audit by other ICO departments”;
- organizations determined by investigations of the ICO Investigations Team [2].
How will the process work?
The process will work as follows:
- “After the confirmation of the audit, an introductory meeting will be done between the audit team and the organization;
- Then, a formal letter of engagement including the scope of the audit will be issued;
- In the stage of document review, before the audit, policies and procedures related to the scope of the audit will be requested and reviewed by the audit team;
- Before the audit, key members and relevant processes will be determined;
- The interviews, group meetings or presentations will be scheduled;
- The audit will begin with an opening meeting in which the process and practical considerations will be discussed;
- Communication between the audit team and the key staff will be ensured to assess operational effectiveness and the following will supplement these sessions:
- Potential data analysis, reviewing KPIs, examples of selected processing of personal data within the AI system, testing of controls;
- In case of a data breach, the organization will be informed about the necessary actions and next steps;
- Key documents, records and systems will be accessed;
- Communication of concern areas will be ensured at the end of each day;
- A closing meeting focusing on major concerns, an overview of the audit and the next steps will be arranged;
- A draft report covering an assurance rating for each scope area, non-conformities, associated risk and prioritized recommendations;
- The organization will decide whether it will accept the recommendations and prepare an action plan;
- Finally, a final report and its executive summary will be provided [2].
Writer : Gamze Büşra Kaya
References
[1] “Who we are | ico - information commissioner's office.” [Online]. Available: https://ico.org.uk/about-the-ico/who-we-are/. [Accessed: 23-Jan-2023].
[2] “A guide to ICO audit artificial intelligence (AI) audits.” [Online]. Available: https://ico.org.uk/media/for-organisations/documents/4022651/a-guide-to-ai-audits.pdf. [Accessed: 23-Jan-2023].



